Configuring authentication settings and profiles
Authentication profiles allow hosts to restrict meeting participants and webinar attendees to signed-in users only and even further restrict it to Zoom users whose email addresses match a certain domain. This can be useful if you want to restrict your participant list to verified users or users from a certain organization. Additionally, you can prevent users in specified domains from joining meetings or webinars.
Notes:
- If using authentication exceptions with a recurring meeting series and you edit one of the occurrences in the series, you must resend the authentication exception email to that participant for that edited occurrence. The link for this occurrence is unique to that edited occurrence and will not apply to other sessions in the series.
- You can also apply authentication profiles to invited webinar panelists.
Requirements for configuring authentication profiles
How to enable or disable authentication profiles
Authentication profiles must be configured at the account level. Once you have configured authentication profiles, you can disable them at the account level and enable profiles at the group or user level, if you do not want to apply it for all members of your account.
Notes:
- Enabling these settings without locking them means the authentication setting is selected by default when hosts schedule a meeting/webinar but they can disable it. Lock these settings to enable these authentication settings by default and prevent hosts from disabling them.
- If a participant does not have a Zoom account, they will not be able to join the meeting or webinar if this setting is enabled.
Account
To enable or disable Only authenticated users can join meetings for all users in the account:
- Sign in to the Zoom web portal as an admin with the privilege to edit account settings.
- In the navigation menu, click Account Management then Account Settings.
- Click the Meeting tab.
- Under Security, click these toggles to enable or disable it:
- Only authenticated panelists can join webinars: Panelists will need to sign in to the Zoom account associated with the email address that was invited to the webinar. Panelists that fail to do so will see a pop-up notification informing them that they need to sign in to the account associated with the invited email address.
- Only authenticated meeting participants and webinar attendees can join meetings and webinars: Meeting participants and webinar attendees will need to authenticate using one of the authentication methods prior to joining a session.
- If a verification dialog appears, click Enable or Disable to verify the change.
- (Optional) If you want to make this setting mandatory for all users in your account, click the lock icon
 , and then click Lock to confirm the setting.
, and then click Lock to confirm the setting.
Groups
To enable or disable Only authenticated users can join meetings for a group of users:
- Sign in to the Zoom web portal as an admin with the privilege to edit groups.
- In the navigation menu, click User Management then Groups.
- Click the applicable group name from the list.
- Click the Meeting tab.
- Under Security, click these toggles to enable or disable it:
- Only authenticated panelists can join webinars: Panelists will need to sign in to the Zoom account associated with the email address that was invited to the webinar. Panelists that fail to do so will see a pop-up notification informing them that they need to sign in to the account associated with the invited email address.
- Only authenticated meeting participants and webinar attendees can join meetings and webinars: Meeting participants and webinar attendees will need to authenticate using one of the authentication methods prior to joining a session.
- If a verification dialog appears, click Enable or Disable to verify the change.
Note: If the option is grayed out, it has been locked at the account level and needs to be changed at that level. - (Optional) If you want to make this setting mandatory for all users in the group, click the lock icon
 , and then click Lock to confirm the setting.
, and then click Lock to confirm the setting.
How to create an authentication profile
- Sign in to the Zoom web portal as an admin with the privilege to edit account settings.
- In the navigation menu, click Account Management then Account Settings.
- Under the Security section, verify that Only authenticated meeting participants and webinar attendees can join meetings and webinars is enabled and then click Add Configuration.
- Under Select an authentication method, choose one of the following options:
- Sign in to Zoom: Allows any user to join the meeting or webinar, as long as they are signed into their Zoom account.
- Signed-in users in my account: Allows any signed-in user in the account to join the meeting or webinar.
- Sign in to Zoom with specified domains: Allows you to specify the rule so that Zoom users, whose email addresses contains a certain domain, can join the meeting or webinar. You can either add multiple domains, using a comma in between and/or use a wildcard for listing domains. You can also upload a CSV file with the domains.
Note: You can't add any domains that are on your domain block list. - Signed in to account associated with invited email: Allows you to require meeting and webinar registrants to join the meeting or webinar signed-in to the account that matches the email they registered with. If they are authenticated with a different account or not authenticated at all, they will be directed to sign-in or switch accounts.
- Sign in to external Single Sign-On (SSO): Allows you to specify a rule so that users need to authenticate through a 3rd-party authentication service.
- Enter a name for the meeting authentication option to help users identify it.
- Click Save.
- (Optional) Click Add Configuration and repeat steps 4-6 to add more authentication options.
How to allow authentication exceptions
If authentication profiles is enabled, admins can allow authentication exceptions to allow guests to bypass authentication to join meetings. For example, if a school authenticates meeting participants against their school IDP, they can create an exception to allow a guest lecturer to join the meeting.
Notes:
- If an admin has blocked a specific domain from joining meetings or webinars, participant(s) matching the blocked domain can bypass the restriction if the host adds them as an authentication exception for the meeting or webinar.
- If using authentication exceptions with a recurring meeting series and you edit one of the occurences in the series, you must resend the authentication exception email to that participant for that edited occurrence. The link for this occurrence is unique to that edited occurrence and will not apply to other sessions in the series.
This feature can be enabled at account or group level. Users can view the setting but not change it.
- Enable authentication profile at the account or group level.
- Under Security, select the check box next to Allow authentication exception.
- Select an option to determine if users who only join by telephone will be allowed to join the meeting if waiting room is disabled.
Hosts will be able to specify authentication exceptions when scheduling a meeting.
How to configure authentication profiles using external authentication
Important: For authentication profiles using Single Sign-On, this must be a separate integration that is not associated with a Zoom SSO integration already. For example:
To configure the profile using external authentication through Single Sign-on:
- Create a new SAML app within your SSO service provider.
- Sign in to the Zoom web portal as an admin with the privilege to edit account settings.
- Enable authentication profiles at the account level.
- Click Add Configuration.
- Under Select an authentication method, select Sign in to external Single Sign-On (SSO).
- Enter the following information:
- Enter a name for the meeting authentication option.
- Sign-in page URL: Sign-in URL provided by the SSO provider
- Identity provider certificate: X.509 certificate provided by the SSO provider
- Issuer (IDP Entity ID): Provided by the SSO provider
- Binding: Select either HTTP-POST or HTTP-Redirect
- SAML attribute mappings (optional): If you are using a different SAML value for email addresses than the standard value name, enter it here.
- Click Save.
- Under Meeting Authentication Options, click SP metadata XML to download the SP metadata.
- Upload the metadata into your SAML app, or open the metadata XML file and copy the following URLs and paste them into the required fields of your SAML app:
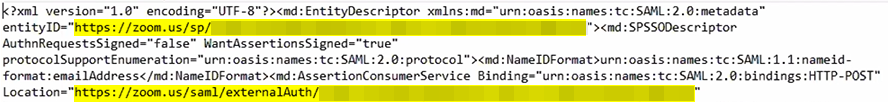
- entityID attribute in the md:EntityDescriptor tag
- Location attribute in the md:AssertionConsumerService tag
The following table lists where you should paste the entityID and Location URLs.
| SSO provider | Field to paste entityID | Field to paste Location |
| G Suite | Entity ID | ACS URL |
| Clever | ENTITY ID | ASSERTION CONSUMER SERVICE URL |
Note: Some Single Sign-On providers, like Okta, require the SP metadata to be generated before retrieving the sign-in URL, IDP certificate, and Entity ID. If you are provider requires the SP metadata first, you will need to fill out the fields with fake data initially, then download the metadata. After that, edit the profile and replace the fake data with the real SSO configuration.
