The Customer Managed Key service allows organizations to provide and manage their own encryption keys for certain customer content stored in the Zoom Cloud. Zoom supports Amazon Key Management Service (KMS), Oracle OCI Vault, or Azure Key Vault. Organizations need to manage the keys with one of these cloud KMS providers. This allows for encryption of applicable content stored in the Zoom Cloud using the keys that the organization controls.
Note: Please refer to our list for more information on all the Zoom services and assets supported with Customer Managed Key.
Administrators can configure Zoom Phone to drop calls if encryption/decryption keys are not available for operation. This option needs to be requested via a Support ticket.
To set up your AWS account, sign up at https://aws.amazon.com/
Create your KMS in the same location/region where you have configured your account data to reside. This is US East 1 region by default.
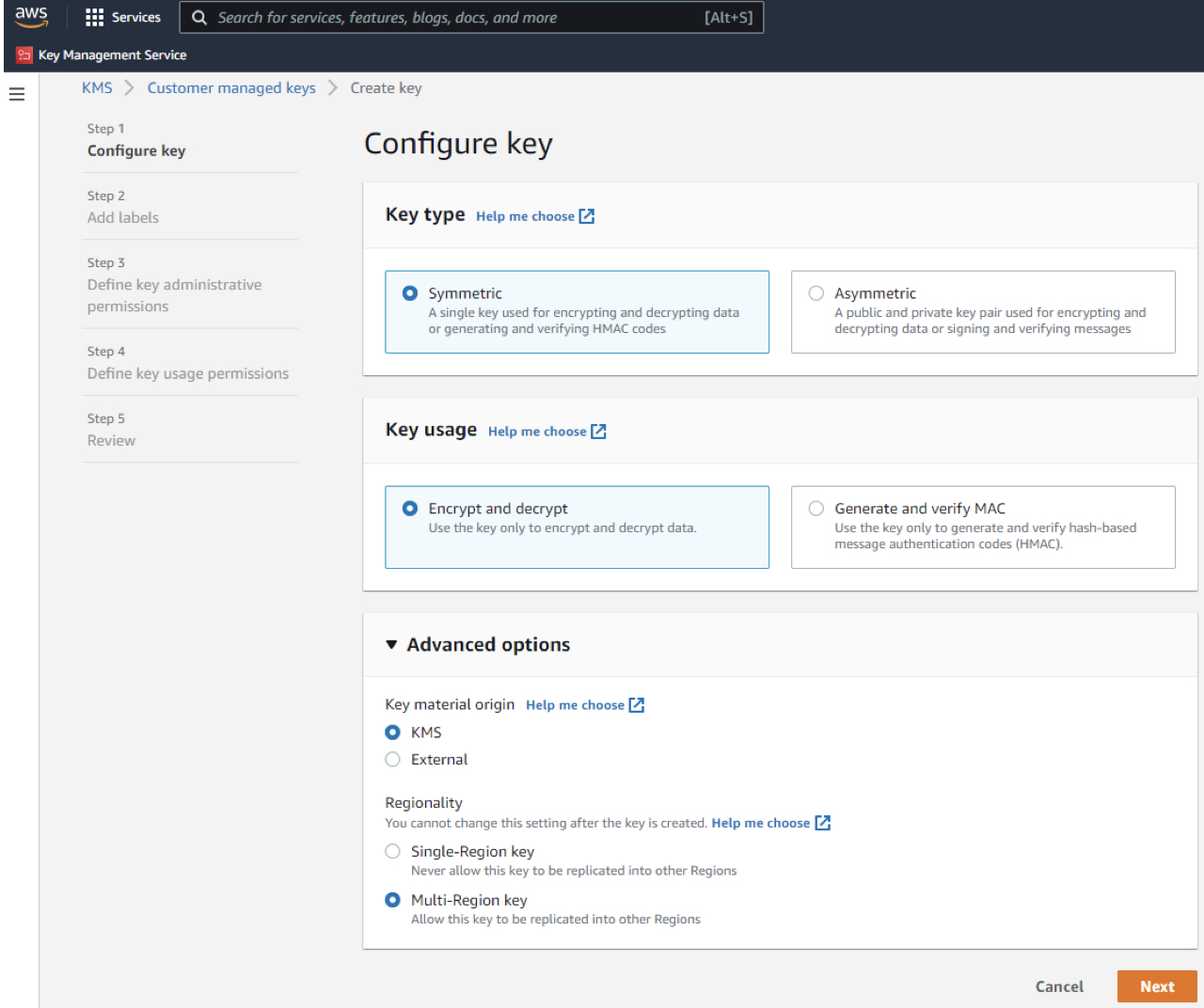
The AWS KMS keys that you create are considered Customer Managed Keys. Customer Managed Keys are KMS keys in your AWS account that you create, own, and manage. Before you get started with Customer Managed Key service in the Zoom cloud, follow the steps below:

In order to configure your key’s policy, go to the Customer Managed Key page in the Encryption Keys section of the AWS KMS management console.
The policy needs to include the following:
There are two ways to add these:
This is an example template of a key policy that you could customize to meet your organization's needs:
{ "Version": "2012-10-17",
"Statement": [
{ "Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::YOUR_AWS_ACCOUNT_NUMBER:root"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Effect":"Allow",
"Principal": {
"AWS": [
"arn:aws:iam::409910850980:root"
]
},
"Action": [
"kms:Decrypt",
"kms:Encrypt",
"kms:DescribeKey",
"kms:GenerateDataKey*"
],
"Resource":"*"
}
]
}
Note: If you enable Multi-region key (MRK), the key policy will be replicated to the MRK secondary region. However, if you manually edit the MRK primary key policy you will need to ensure those changes are also manually added for the MRK replica key as well.
If you plan to enable search data encryption, you also need to allow the CMK search service to access your organization's key.
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::735735407888:role/csms@prod_searchmanage_aw1"
]
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant",
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}
Users with assigned Customer Managed Key licenses will have their data encrypted.
To learn more about different approaches to managing keys, such as auto key rotation, manual key management, and external HSM key management, see Key management concepts.
Access to the customer’s key at all times is critical to create and access any content which has been selected to be secured by CMK. Zoom not only encourages the use of replicated keys, but also supports a global "fallback control" option. If enabled and the customer’s key is not available for any reason, CMK falls back to a Zoom provided backup key for encryption. Once the customer’s key becomes available again, CMK will re-encrypt all content with the customer’s key. If the fallback option is not enabled and the customer’s key is not available, content will not be stored.